Origo
The newest iteration of Xahau DocProof has an additional function called Origo!
Memory Refresher
On May 10, 2025, I wrote about Xahau DocProof, a blockchain-based notary service created by Andrei Rosseti.
Traditional notary services, even the large ones that were created to leverage the power of the Internet and its new ability to communicate information instantaneously instead of through snail mail, still rely on central authorities.
Xahau DocProof changes all that.
With the first iteration of his solution, Andrei offered a service whereby documents would still need to be stored (somewhere), but the cryptographic proof of (signature) authenticity would reside on the Xahau blockchain.
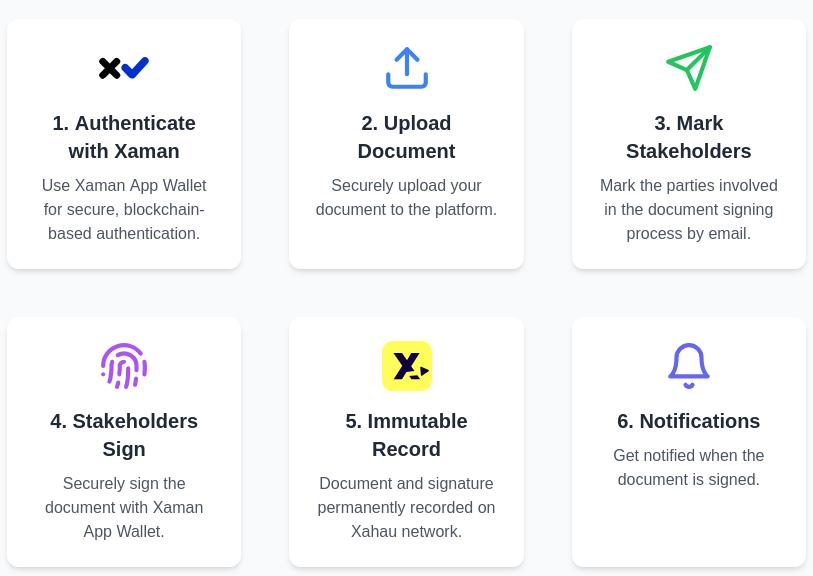 Xahau DocProof
Xahau DocProof
This project realized the vision of what many of us in crypto have been wanting to see for years; the leveraging of blockchain immutability to move trust in a third party to a decentralized ledger.
What Xahau DocProof (Version One) Did
The original Xahau DocProof is used when there are two or more individuals that need to verify that a document has been 'signed' by a party to an agreement, contract, or other formal document. So, to summarize the important points, the Xahau DocProof (first iteration) contains the following characteristics:
- Immutable cryptographic record
- On-chain (public, permanent)
- Trust during document upload & storage step
- Xaman wallet integration
There is also a small, almost-imperceptible fee associated with the transaction, as all transactions on Xahau require a minute bit of XAH, it's native token.
Origo
In his own words, Andrei indicated:
"Origo was born to sign & verify docs for one person"
"Xahau DocProof (overall) was born to be used with MORE than one (person) to sign & verify..."
Origo is a way to verify that a document is the 'real deal' ... that the document you're looking at is, in fact, the right one, and that it came from the person who you think it came from.
So how does Origo do its magic under the hood?
The High Points
One of the amazing things about Origo, is that no on-chain cryptographic storage is necessary, unless the user wants to see it put there.
Essentially, Origo uses a system that was pioneered by the XRP Ledger through the use of a 'TOML' file. A TOML file is a specific type of 'key-value' markdown-language text file that a company or 'domain owner' can place somewhere on their web server.
 Origo
Origo
Origo checks to make certain that the domain indicated is part of the document, and is, in fact, the correct domain with the TOML file. These two items - one as part of the document, and one as part of a web domain - must match up, in addition to validating the cryptographic hash of the document in question.
The person that has custody over the document must 'hash' it, which provides a unique digital fingerprint of that document.
Straight From The Architect
While high-level business descriptions are valuable in abstracting the details, many XRPL and Xahau developers will be curious about the specifics.
Here is Andrei's own detailed description of the steps that happen under the hood:
- You’re logged in with a wallet
- You sign the document (off-chain)
- Origo (locally) delivers a PDF with a byterange that includes the result of the signed operation — a hash of the signature (in hex)
- The address added along with a QR code on the last page of the PDF takes you to the validation portal, which runs entirely locally, without transmitting any files
- When you drag the file in, the system captures the hex hash of the signature, the SHA-256 hash of the file, and sends them to an Origo API for validation together with the rAddress
- Origo fetches the domain from the rAddress, validates the TOML, and if the rAddress is listed in the TOML, it proceeds
- Origo derives from the hex signature the user’s rAddress and also checks whether the SHA-256 hash matches the transaction derived from the signature
- If everything matches, the response is VALID — otherwise, INVALID
Essentially, if the sender goes through the steps listed, the receiver can use Origo to validate that the document is 'legit'.
A real-world example would be a supplier sending a bill to a customer. The sender and receiver of the bill could use Origo to make certain that the invoices are considered legitimate.
Open Source
Trust is lacking in many centralized solutions, and the era of black-box software solutions is drawing to a close. Knowing this, Andrei has decided to publish his code rather than keep it proprietary ... an interesting gamble that might be wise in retrospect.
He has compartmentalized the code he developed into five, high-level categories:
- Node.js (API)
- Express (API)
- Next.js (XApp)
- C (Smart Contract)
- Docker (Containerization)
Any stakeholder can access the public Github repository here: github.com/rosseti/xahau-docproof
User Flow
If you want to see the entire flow from the user perspective, it may answer some questions in a more intuitive fashion. Here is a video that demonstrates the flow:
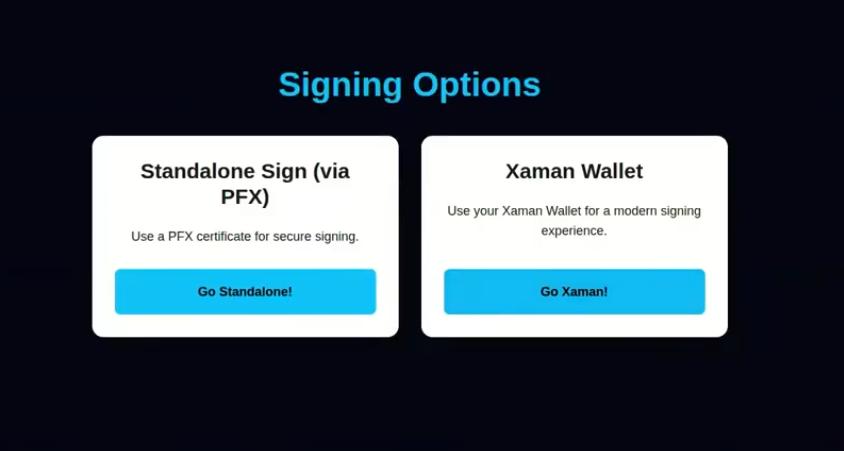 Still Image From 'Meet Origo' On YouTube
Still Image From 'Meet Origo' On YouTube
Video Link: Meet Origo
Important Note: Using Xaman simplifies the process. But ... for more independent users, an individual-signing path is also possible using PFX libraries.
My guess is that the Xaman pathway will be the most popular, due to its simplicity and smooth UI.
Cryptographic Proof Usage
The fascinating part of the Origo tool addition to Xahau DocProof is that no on-chain transaction is necessary, eliminating even the microscopic transaction fee associated with the original version of Xahau DocProof.
Instead, cryptographic libraries are used on both pathways; through Xaman or through independent use.
Hook Store Integration?
During the annual Xahau birthday celebration, it was widely agreed that a cryptographic proof of code authorship - of some kind - was a preferred part of the hook store requirements.
The approach for 'auditing' code is still not well-defined, but the larger group agreed that using some sort of verification of authorship would be an important part of any proposed solution for the hook store. Bounties were communicated at the end of the discussion, but have yet to see a formal written communication.
Origo's Future
Electronic signature and cryptographic document verification are growing fields of technology. Centralized solutions have cornered the bulk of the traditional financial market in this category, but the new blockchain entrants in the space may be a welcome addition by stakeholders.
My initial impression is that Origo - and Xahau DocProof - may grow to something very large if any of several things happen:
- A large corporate sponsor integrates it into their own product
- On-chain DID is finally addressed so it can be integrated with DocProof
- Individual users begin to use it to verify important documents
The phrase 'we are still early' is thrown around by speculators in layer one digital assets; but in the case of Origo and Xahau DocProof, I'm confident that that same idea applies to blockchain notary systems. X>
Sources:
https://x.com/Hodor/status/1921208453508293081







