Automated NFT airdrop ( URI Remit )
URI Remit Hook Tutorial
After some encouragement from Satish, I will be sharing some details of the amazing hooks I've been creating here on xpert.page. By publishing these examples and putting them to use on Xahau Mainnet, I hope to encourage others to #GetHooked and explore their own use cases for this account layer of programmability.
The first hook I'll share is the URI Remit Hook, which mints and sends back an NFT whenever an incoming payment is received. This is a simplified version of the URI-Token-Remit created by @Cbot_Xrpl, designed for use as a thank-you card on my daughters xpert.page.
Getting Started
 Automated NFT Airdrop
Automated NFT Airdrop
To keep things as simple as possible, we'll use three tools: Pinata IPFS, XRPLWin, and Hex Visualizer. This tutorial was created on testnet, but when you're ready to deploy to mainnet, the only changes required will be the Hook Hash and possibly the account you're installing it on.
Tools and Resources
- Wallet Generator: https://test.xahauexplorer.com/create/
- Wallet Funding: https://test.xahauexplorer.com/en/faucet
- Hook Hashes:
- Testnet:
8F9F3EAC7945092D65F26D96BDC8E336F95F44BBFB381F18924E58A69DF62DD2 - Mainnet:
2D282A0F475B79510BE5B6CAEA2C655571A6B229BC36F8EB7B5E2650BE2EA93F
- Testnet:
Required Tools
-
Pinata IPFS - https://app.pinata.cloud
This service will host our image files and metadata. The free tier supports up to 500 files, with competitive options for expanding collections in the future. -
XRPLWin - https://testnet.xrplwin.com/
XRPLWin's hook dashboards are exceptional, offering tools to take your testnet project to mainnet. It's also great for debugging on testnet and managing hooks on mainnet. -
Hex Visualizer - https://transia-rnd.github.io/xrpl-hex-visualizer/
This tool converts strings into the correct hex formats required for our parameters. If your hook compilation fails, double-check your hex codes here.
Pinata Setup
Setting up files for the remit hook can be tricky, as the hook expects a predetermined URI length. The best approach is to host the images first, then create a folder of JSON files referencing them.
 Pinata Fileserver
Pinata Fileserver
-
Sign up for Pinata and select the free tier. Upload the images you want to use. Once uploaded, you'll receive a CID (Content Identifier), which uniquely identifies each image.
-
Create a new folder and download the JSON template from HERE. Customize the JSON file with unique identifiers and update the image CID path to match the CID of the uploaded image. Create as many files as needed, ensuring consistent file name lengths (e.g.,
000001.json,000002.json,000003.json).Example JSON:
{ "name": "HandyHooks - Thank you remit", "description": "This is a thank you gift for your donation through the xpert.page platform, we appreciate your support", "image": "ipfs://YOUR_IMAGE_CID_GOES_HERE", "external_link": "https://xpert.page/handy_4ndy", "attributes": [ { "trait_type": "Message", "value": "Thank you for your support, we appreciate it!" } ], "edition": "001" } -
Upload the folder to Pinata to ensure uniform URI lengths. Example URIs:
ipfs://bafybeifhrrj3pvotihooenwljj4rreskvdb6dahxwq7cskpao73ishk2p4/000001.jsonipfs://bafybeifhrrj3pvotihooenwljj4rreskvdb6dahxwq7cskpao73ishk2p4/000002.jsonipfs://bafybeifhrrj3pvotihooenwljj4rreskvdb6dahxwq7cskpao73ishk2p4/000003.json
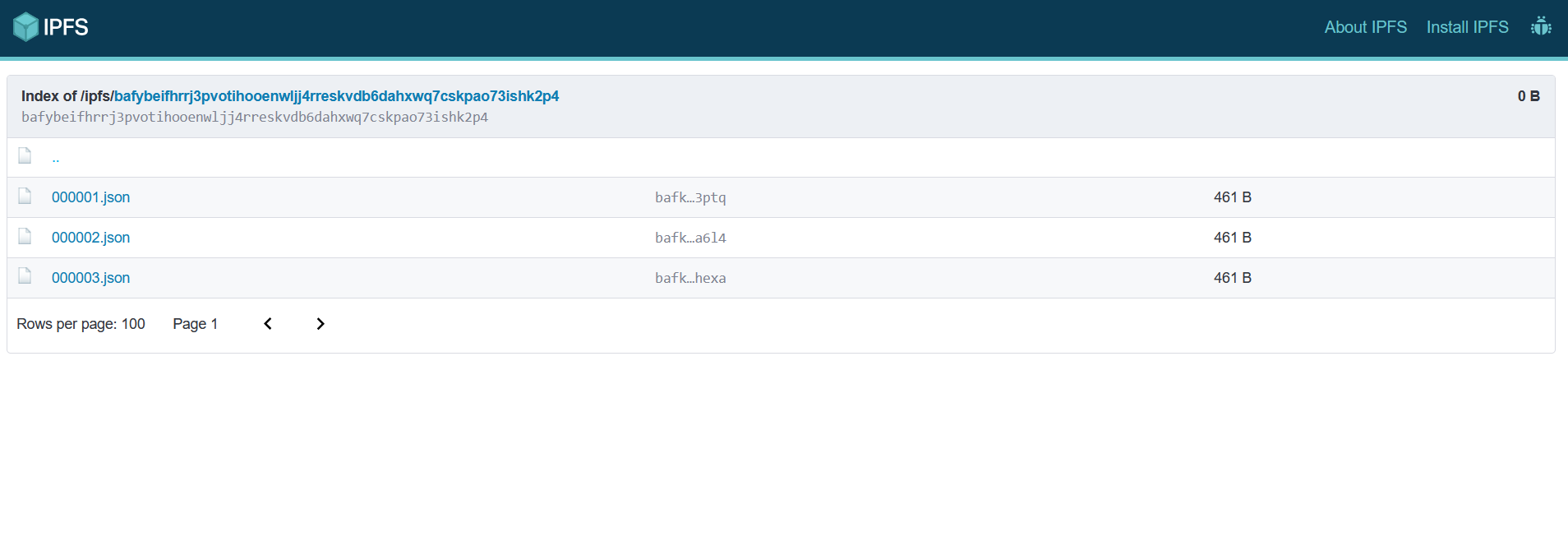 IPFS folder referance
IPFS folder referance
Hook Installation
XRPLWin's dashboards simplify the process significantly. If you encounter issues, this is the go-to place. We'll install and set up the hook here.
-
Switch the connection to Xahau Testnet in the top-right corner of XRPLWin. Enter your testnet account seed or sign in with Xaman if deploying to mainnet.
-
Navigate to the tools section.
-
Focus on the Raw Transaction Sender and Install Hook from Hash. Use one of the following hook hashes:
- Testnet:
8F9F3EAC7945092D65F26D96BDC8E336F95F44BBFB381F18924E58A69DF62DD2 - Mainnet:
2D282A0F475B79510BE5B6CAEA2C655571A6B229BC36F8EB7B5E2650BE2EA93F
- Testnet:
-
Click Install from Hook Hash, insert the appropriate hash, and proceed to the raw JSON transaction builder. The hook details will be pre-filled, as shown below:
 XRPLWin's Install from Hook Hash
XRPLWin's Install from Hook Hash
{
"TransactionType": "SetHook",
"Account": "YOUR_CONNECTED_rADDRESS",
"Flags": 0,
"Hooks": [
{
"Hook": {
"HookHash": "8F9F3EAC7945092D65F26D96BDC8E336F95F44BBFB381F18924E58A69DF62DD2",
"Flags": 1,
"HookOn": "FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF7FFFFFFFFFFFFFFFFFFBFFFFE",
"HookNamespace": "4FF9961269BF7630D32E15276569C94470174A5DA79FA567C0F62251AA9A36B9"
}
}
]
}
-
Submit and sign the transaction to set the hook. Pay attention to the
HookOnfield, which defines the triggers (ttPAYMENTandttINVOKE) for the hook. -
Load the account with the URIs created earlier using Invoke transactions. The hook parameters are submitted as hex strings or
uint64integers. Use the Hex Visualizer to convert or validate inputs.
 XRPL Hex Visualizer
XRPL Hex Visualizer
-
Set the URI length (
URIL :: 5552494C) to match the character length of your URI string. Use a string length tool to calculate. For example, the URIipfs://bafybeifhrrj3pvotihooenwljj4rreskvdb6dahxwq7cskpao73ishk2p4/000001.jsonhas 78 characters (78 :: 000000000000004E).{ "TransactionType": "Invoke", "Account": "YOUR_CONNECTED_rADDRESS", "HookParameters": [ { "HookParameter": { "HookParameterName": "5552494C", "HookParameterValue": "000000000000004E" } } ] } -
Upload URI/NUM pairs for the hook to distribute. Each URI must be submitted individually via Invoke transactions. Convert the URI to hex using the Hex Visualizer and assign a NUM value (e.g.,
1 :: 0000000000000001).
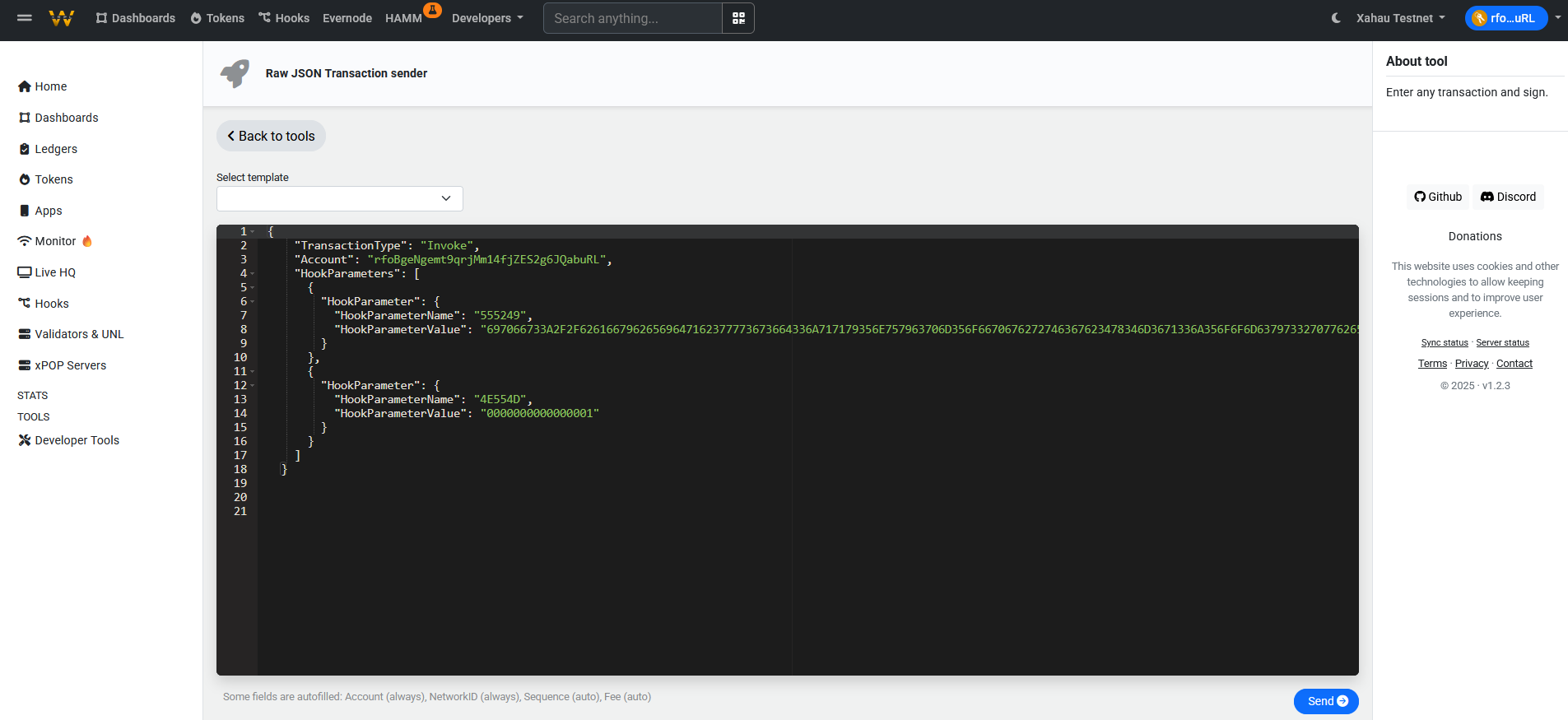 Invoke Raw JSON Example
Invoke Raw JSON Example
Example:
- URI:
ipfs://bafybeifhrrj3pvotihooenwljj4rreskvdb6dahxwq7cskpao73ishk2p4/000001.json - URI Hex:
697066733A2F2F62616679626569666872726A3370766F7469686F6F656E776C6A6A34727265736B766462366461687877713763736B70616F37336973686B3270342F3030303030312E6A736F6E - NUM:
1 - NUM Hex:
0000000000000001
{
"TransactionType": "Invoke",
"Account": "YOUR_CONNECTED_rADDRESS",
"HookParameters": [
{
"HookParameter": {
"HookParameterName": "555249",
"HookParameterValue": "697066733A2F2F62616679626569666872726A3370766F7469686F6F656E776C6A6A34727265736B766462366461687877713763736B70616F37336973686B3270342F3030303030312E6A736F6E"
}
},
{
"HookParameter": {
"HookParameterName": "4E554D",
"HookParameterValue": "0000000000000001"
}
}
]
}
Repete this transaction changing the Value of each hook parameter with the following.
#2 URI HEX: 697066733A2F2F62616679626569666872726A3370766F7469686F6F656E776C6A6A34727265736B766462366461687877713763736B70616F37336973686B3270342F3030303030322E6A736F6E NUM HEX: 0000000000000002
#3 URI HEX: 697066733A2F2F62616679626569666872726A3370766F7469686F6F656E776C6A6A34727265736B766462366461687877713763736B70616F37336973686B3270342F3030303030332E6A736F6E NUM HEX: 0000000000000003
For each new URI, increment the NUM value (e.g., 2 :: 0000000000000002). Take care to convert each URI to hex accurately and verify using XRPLWin's dashboard to detect errors, delete namespaces, or monitor hook activity.
Testing and Debugging
 Test Sucess
Test Sucess
Test the hook by sending a payment from another testnet account to the hook account and observing the results. Monitor hook activity Here for testnet or Here for Mainnet
If you wanted to see the hook code or browse any other examples check out the Hook-101 Collection, this is example 017_InvokeUriRemit.c




